Division of Information Technology and Institutional Planning
Links to Resources, Departments, and Services
News, Events, and Notices
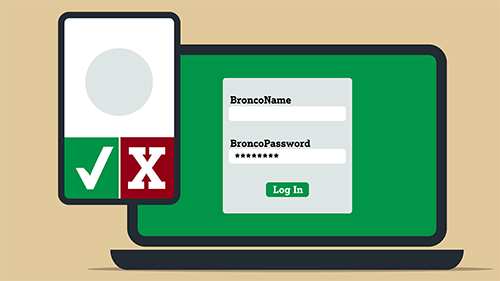
DUO 2-Step Authentication
To protect your privacy and secure your Bronco account, Cal Poly Pomona requires 2-step authentication for all accounts. This process will verify your identity before allowing access to campus systems. The CSU and Cal Poly Pomona are using the DUO application, a third-party smartphone app, for the authentication process, also known as Multi-Factor Authentication (MFA). The DUO app sends a push notification to your device when you log in to verify your identity.
Visit the 2-step authentication page to protect your BroncoIdentity.

eduroam Everywhere: Wi-Fi = eduroam
For a more consistent and secure campus Wi-Fi experience, IT&IP recommends using “eduroam” for your campus Wi-Fi option. Eduroam allows you to use your own CPP credentials to access Wi-Fi at numerous educational institutions worldwide.
The Guest Wi-Fi network supports the needs of temporary visitors to the campus. Users of the Guest Wi-Fi network will be prompted to enter their cellphone number in order to receive a security token that allows them access to the network for 24 hours.
For more information, go to the Wireless Access page in eHelp or contact the IT Service Desk.