To conduct a cutting-edge cyber-threat intelligence research that will impact academia and industry, our lab currently investigates the following areas:
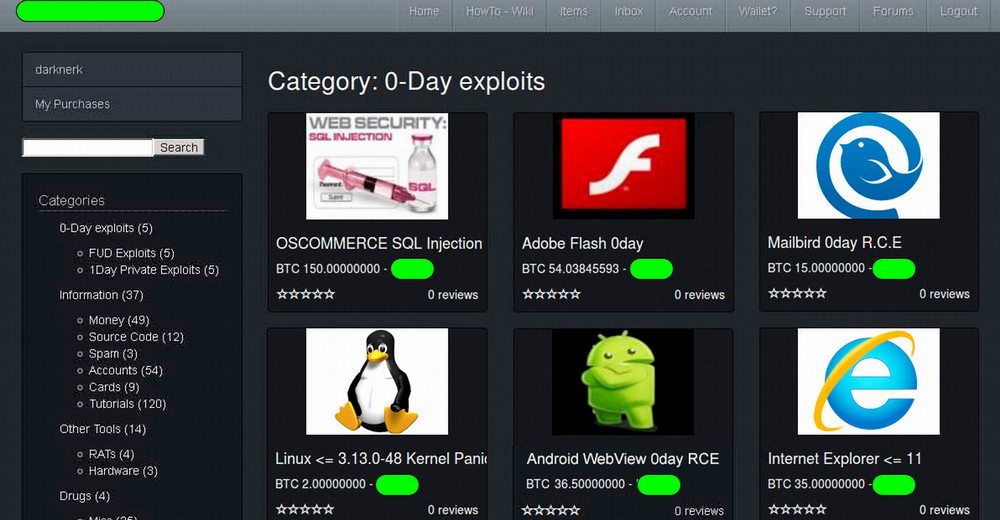
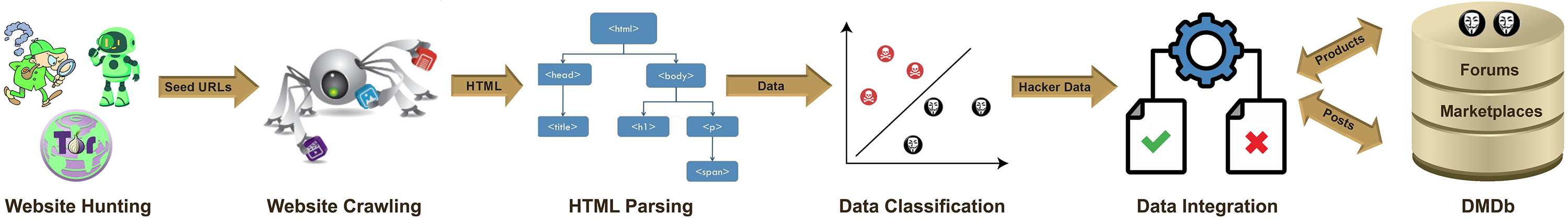
Dark Miner: Cyber-threat intelligence platform designed to support the systematic collection and analysis of adversarial activity from online hacker communities. The project focuses on extracting signals from forum discussions, marketplaces, and related online environments to characterize emerging malicious technologies, services, and attacker capabilities. DarkMiner underpins the creation of a large-scale criminal hacking dataset, DMDb, which is used to study threat evolution, exploit development, and adversarial behavior in cybercrime ecosystems. DMDb is made available to qualified researchers under controlled access for academic research purposes.
|
 |
|
 |
Project awarded by the NSF Computer and Information Science and Engineering Research Initiation Initiative (CRII) Secure and Trustworthy Cyberspace (SaTC) in 2023. |
|
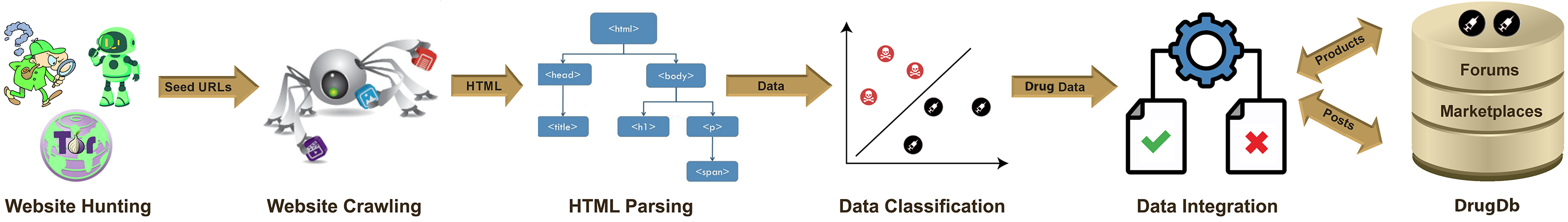
Drug Miner: Drug-threat intelligence platform designed to support the systematic collection and analysis of online illicit drug-market activity. The project focuses on extracting signals from marketplaces, forums, and related online environments to characterize trafficking operations, vendor behavior, and market dynamics. DrugMiner underpins the creation of a large-scale drug-trade dataset, DrugDb, which is used to study the relationship between online drug markets and real-world drug-related criminal activity. By integrating online market signals with public crime and incident data, the project supports research on trafficking patterns, market evolution, and associated risks to public safety.
.
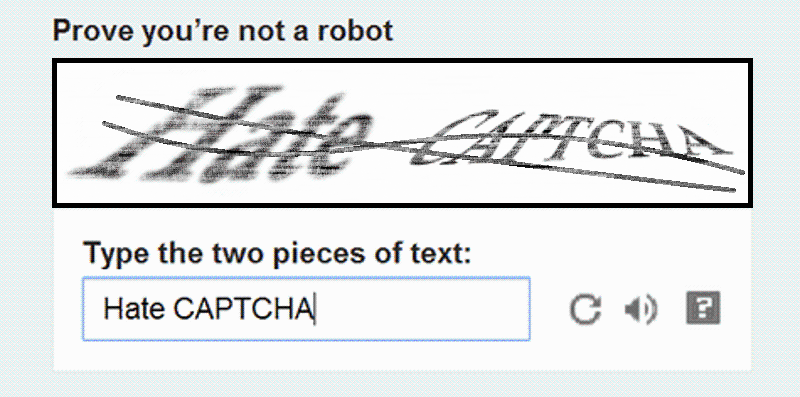
CAPTCHA Solver: Project designed to enable reliable data collection from online environments that employ CAPTCHA-based access controls. Many adversarial and illicit platforms deploy CAPTCHAs to restrict automated access, limiting large-scale and longitudinal analysis. This project develops automated CAPTCHA-solving techniques that support continuous and scalable data acquisition from publicly accessible content, enabling downstream analysis for ATI research.
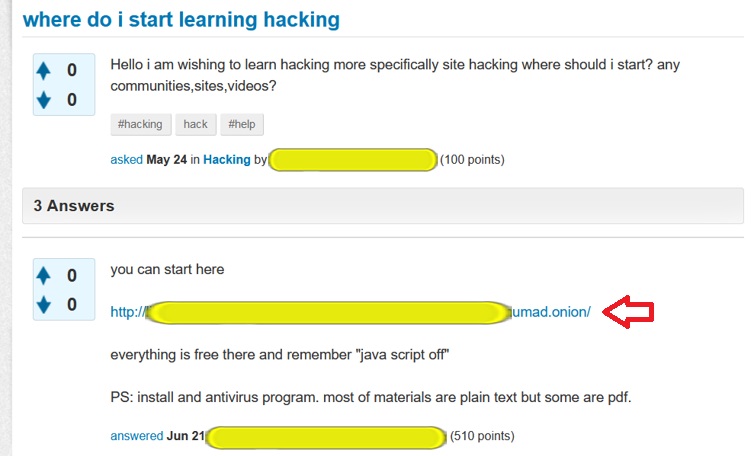
Site Discovery Automation: Project designed to automate the identification of previously unknown adversarial websites referenced within online forums and discussion platforms. The project analyzes hyperlinks embedded in posts, together with their surrounding context—such as neighboring messages and landing-page characteristics—to assess whether a referenced site represents a relevant target for further data collection. This capability supports the continuous expansion of threat intelligence datasets and is applicable across multiple ATI domains.
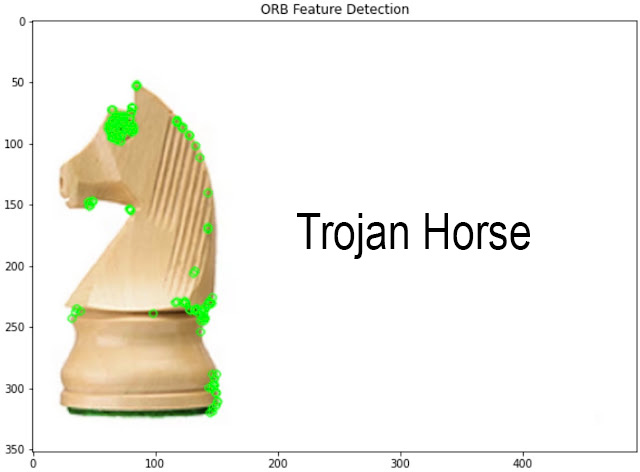
Image Analyzer: Project designed to support the analysis of visual content collected from adversarial online environments while addressing ethical and legal constraints. Instead of retaining raw images, the project focuses on deriving intermediate object-level representations prior to encryption, enabling similarity analysis without preserving original pixel data. This capability allows the identification of recurring visual patterns and shared artifacts across platforms, supporting ATI research in a privacy-preserving manner.
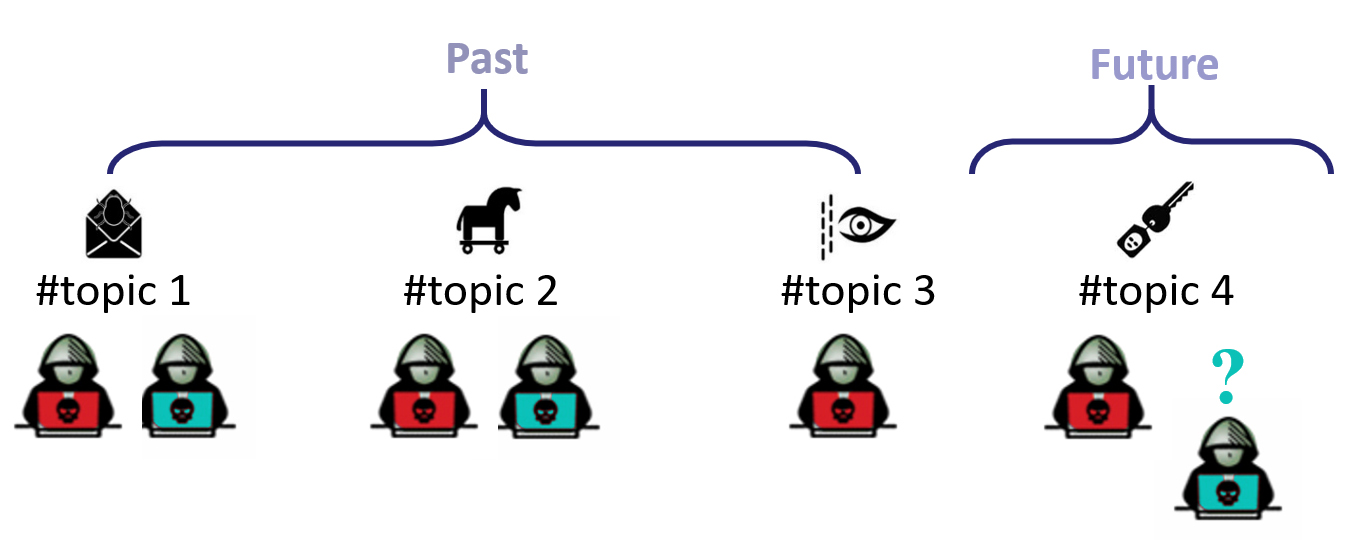
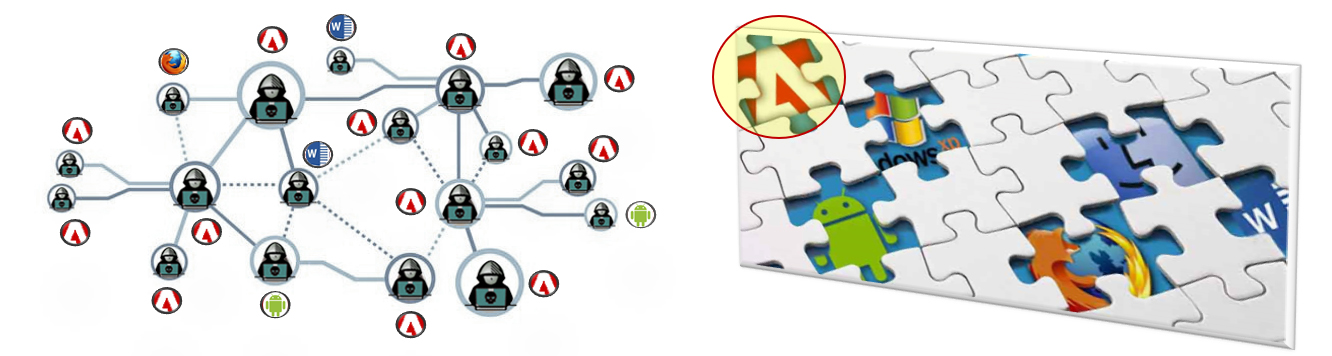
Key Actor Identification: Project focused on identifying highly influential individuals within adversarial online communities whose activity disproportionately shapes threat development and adoption. By characterizing differences in expertise, connectivity, and influence across participants, the project aims to highlight actors who play a central role in fostering emerging threats. This capability supports early warning and prioritization by focusing attention on influential actors across different ATI settings.
Adversarial Engagement Prediction: Project focused on modeling how participation, influence, and adoption behaviors evolve within adversarial online communities. The project examines how influential actors disseminate information, recruit collaborators, and promote artifacts such as tools, services, techniques, or traded products, shaping collective engagement over time. By treating observed engagement dynamics as early behavioral signals, this capability supports anticipation of future activity patterns and is also applicable across different ATI settings.
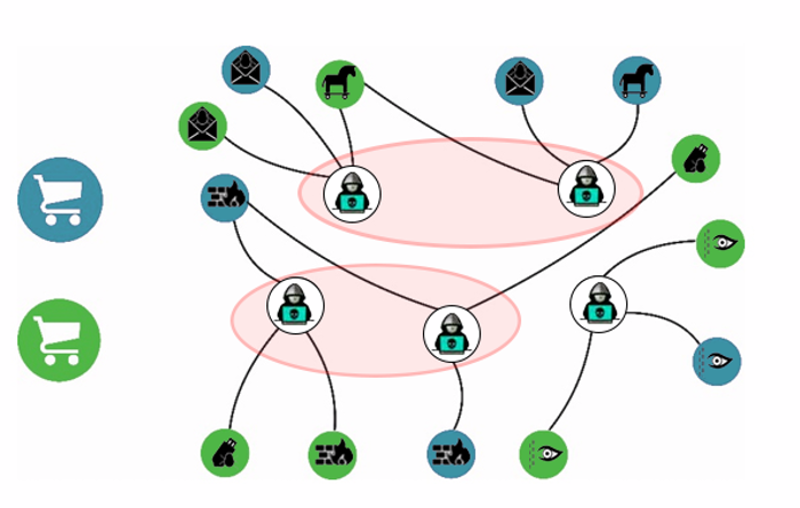
Adversarial Vendor Community Detection: Project designed to identify and analyze communities of vendors within adversarial online marketplaces to understand shared expertise, specialization, and market structure, supporting anticipation of emerging activity patterns across multiple ATI settings.
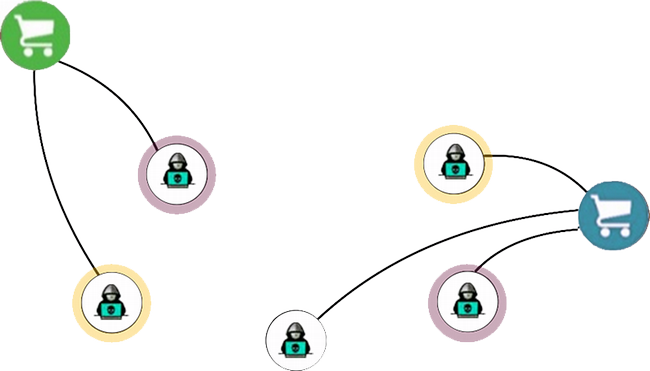
Vendor Alias Attribution: Project focused on linking multiple aliases used by the same underlying actor across adversarial online marketplaces. The project analyzes vendor profiles, offerings, and behavioral patterns to attribute distinct identities to a common source despite deliberate obfuscation. This capability supports a more accurate understanding of actor persistence, specialization, and market behavior and is applicable across different ATI settings.
Vulnerability Exploitation Prediction: Project focused on anticipating which disclosed software vulnerabilities are likely to be exploited in the near future. The project addresses limitations of traditional vulnerability scoring systems by modeling signals related to adversarial interest and activity, enabling more effective risk assessment and patch prioritization. This work supports proactive cyber-threat intelligence by identifying vulnerabilities that warrant early attention before exploitation becomes widespread.
Identification of Zero-Day Exploits: Project focused on anticipating exploit development for disclosed software vulnerabilities that lack an effective vendor patch and therefore exist within a zero-day exposure window. The project aims to identify early indicators that such vulnerabilities are being weaponized or traded before mitigation becomes available, supporting proactive risk assessment and patch prioritization in cyber-threat intelligence.
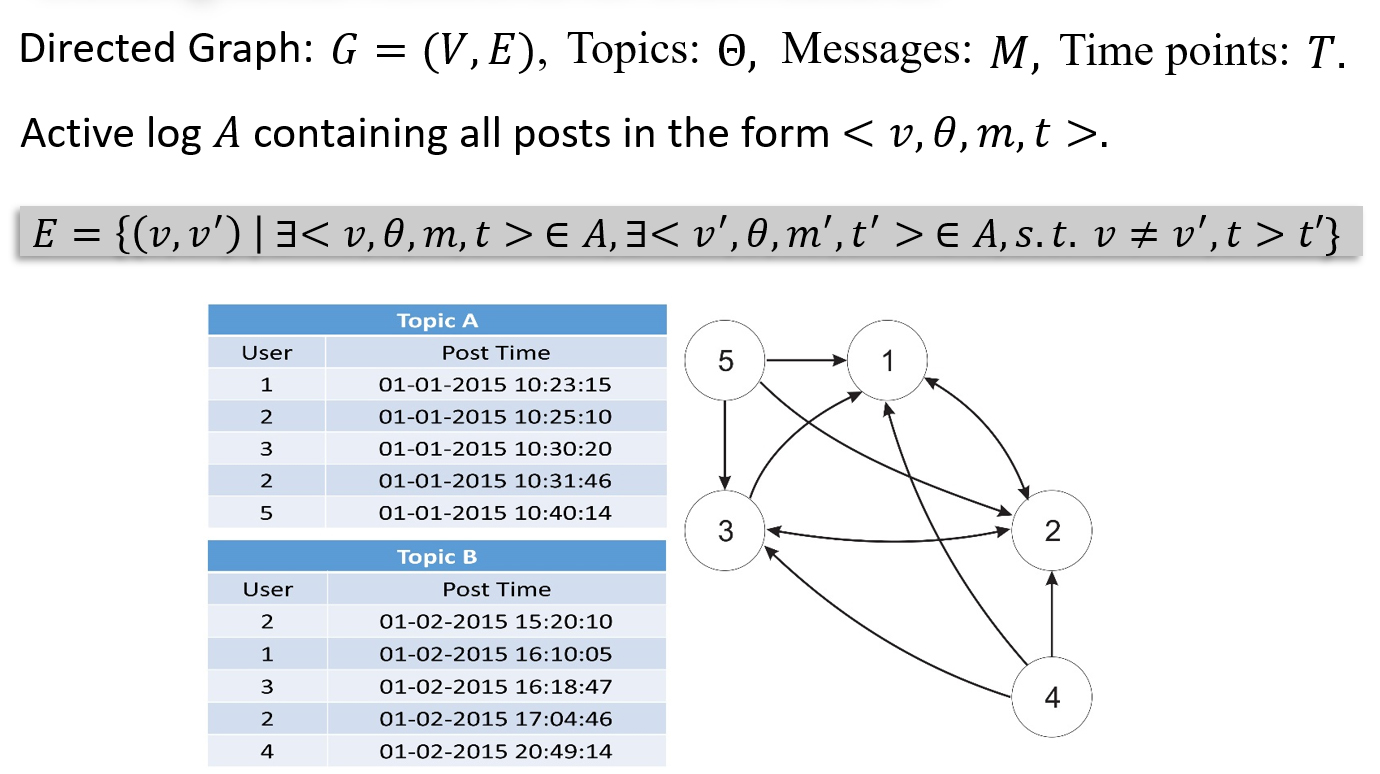
Adversarial Network Reconstruction: Project focused on inferring the underlying interaction networks of participants within adversarial online environments. Because communication in these settings is often fragmented and loosely structured, the project aims to reconstruct network relationships beyond explicit reply or interaction markers. By deriving latent interaction signals from discussion content and activity patterns, this capability enables more accurate approximations of community structure and information flow. The reconstructed networks support downstream analysis across multiple ATI contexts.
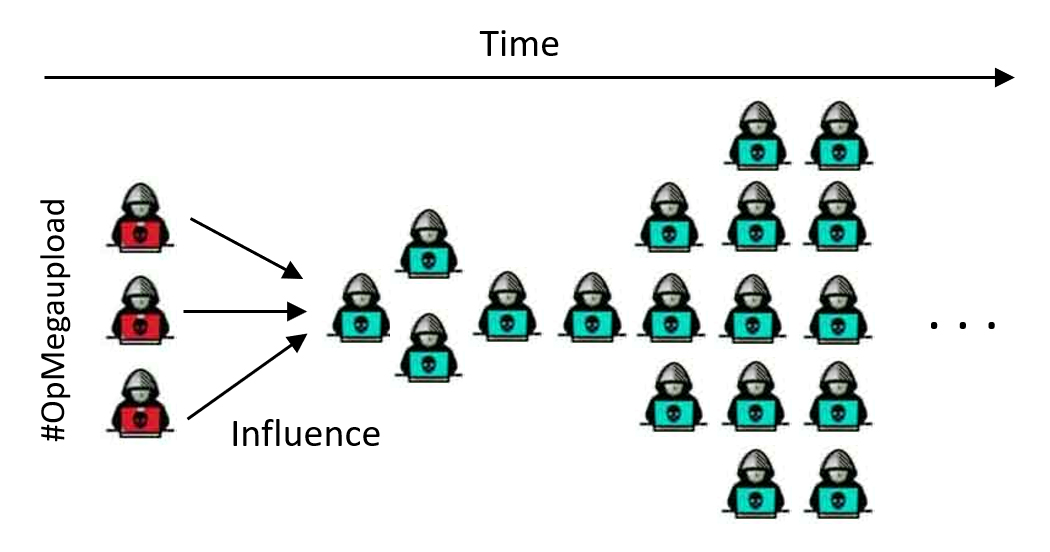
Threat Cascade Prediction: Project focused on modeling how information, offerings, or narratives propagate within adversarial online communities and identifying early signals of rapid adoption. By analyzing diffusion dynamics and influence patterns, the project aims to anticipate which threads, messages, or artifacts are likely to trigger large-scale engagement. This capability supports early warning by highlighting emerging cascades that may signal coordinated activity or mass adoption trends and is applicable across different ATI settings.