Mohamed El-Hadedy Aly - Excellence: Encrypted

In today’s data-drenched world, so many of our communications are digitally encrypted for security. But there is nothing cryptic about electrical and computer engineering assistant professor Mohamed El-Hadedy Aly, Ph.D. and his passion for safeguarding digital communication. Aly is an internationally recognized cybersecurity expert dedicated to helping the world take a quantum leap forward— and to keeping students on the leading edge.
A man of science
Aly was born in Egypt where he received both his undergraduate and master’s degrees. He worked for several years as a scientist at an Egyptian nuclear reactor in the areas of control and security.
He earned his doctorate in Norway and worked on digital security for a nuclear power plant. After that, he joined Atmel’s Norway division to design and test chips as a senior design engineer. Years later, he moved to the United States to work as a scientist for the University of Virginia and University of Illinois at Urbana-Champaign in network security reconfigurable computing.
He came to California and Cal Poly Pomona in 2018 for the opportunity to upload his deep knowledge into the minds of eager students. He also yearned to realize his vision: to help make our college a seedbed of innovation, and our students its beneficiaries.
“The U.S. has always been a top-ranked R&D force involved in so many leading-edge discoveries,” Aly says. “So, we have to continue that legacy and stay ahead of the curve. The best way to do that is to keep cranking the wheels of curiosity in students’ minds.”
Making a quantum leap
Guided by that vision, Aly set his students on a mission to address a looming threat facing the entire world: security vulnerabilities posed by the rise of quantum computers.
 Because quantum computing is so much faster than its conventional counterpart, it can “crack” encrypted communications easily. Currently, we are in a so-called Post-Quantum Era, where the science is only in limited use. Thus, the threat to digital communications at large is limited. Yet once the technology attains widespread adoption all that changes. We then risk compromising things that depend on current encryption measures: nuclear power plants; banking; satellite communications; medical devices, and much more. That threat could literally paralyze certain realms of our society.
Because quantum computing is so much faster than its conventional counterpart, it can “crack” encrypted communications easily. Currently, we are in a so-called Post-Quantum Era, where the science is only in limited use. Thus, the threat to digital communications at large is limited. Yet once the technology attains widespread adoption all that changes. We then risk compromising things that depend on current encryption measures: nuclear power plants; banking; satellite communications; medical devices, and much more. That threat could literally paralyze certain realms of our society.
“The U.S. has always been a top-ranked R&D force. So, we have to continue that legacy and stay ahead of the curve. The best way to do that is to keep cranking the wheels of curiosity in students’ minds.” – Mohamed El-Hadedy Aly, Ph.D., electrical and computer engineering assistant professor
Aly has an extensive research record in cryptography, with over 20 published papers and confernce presentations on the subject. Further, federal organizations like the U.S. Air Force, Department of Energy and the U.S. Navy have all awarded Aly fellowships to study post-quantum computing. In short, Aly is an expert absorbed by the field.
Students rise to the challenge
Bringing his vast understanding of the quantum computing threat to the classroom, Aly set students to work on coming up with a solution. But not just any solution.
Instead, one that would use minimal resources so it can be implemented quickly.
“[Professor] Aly was very helpful in guiding us toward a real-world application,” says student Ian Lieu (’21, electrical engineering; computer engineering) about the award-winning efforts of his team.
Aly split his class into two groups. The first team was tasked with solving the cryptography part of the puzzle. After intense research inspired by Aly they arrived at a hash-based signature algorithm, the kind widely used in cryptocurrency today.
The second team was challenged to apply that algorithm to a technology familiar to anyone using a smartphone, wireless speaker, keyboard or mouse: Bluetooth. Easier said than done. First, Bluetooth has weak security. Second, much of the technology on Bluetooth devices is proprietary, leaving few resources to accommodate a universal solution.
Nevertheless, the team came up with a novel idea: move the hash-based cryptography algorithms to a partition, thereby enhancing security without sacrificing performance or resources for other tasks.
The solution was so inventive that the team won two major competitions. They took home honors at the 2021 CPP Student Research, Scholarship & Creative Activities (RSCA) conference, and then went on to win the system-wide California State University Student Research Competition later that year.
Notwithstanding the tremendous talent and efforts of the students, this engineering breakthrough owed much to Aly’s teaching philosophy—one emphasizing not just course material but a different way of thinking.
“I teach my students to become like philosophers in a way that they will be successful no matter if they're in an exposition or deposition.”
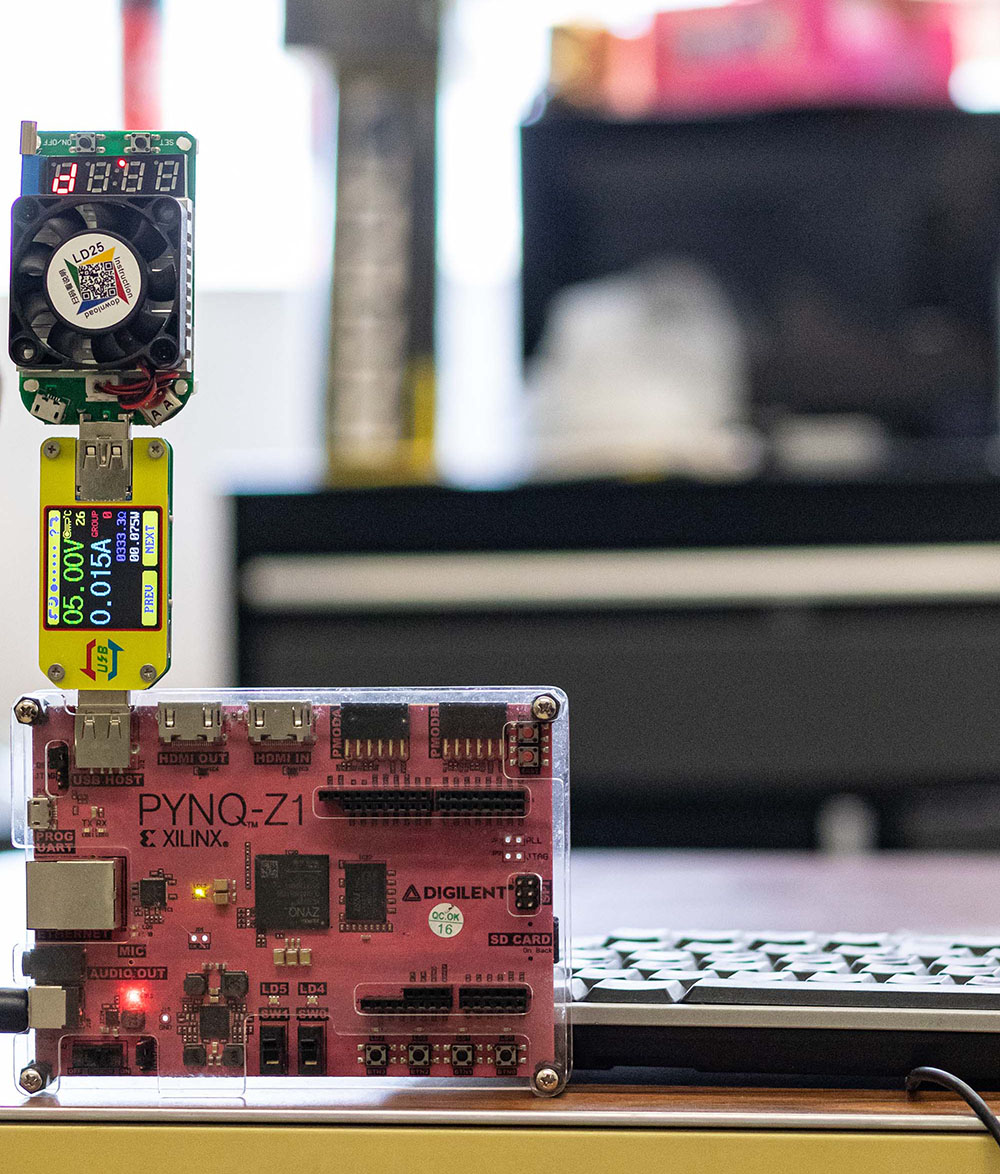
Second photo: The winning device that ran the team's hash-based cryptography algorithm for a Bluetooth device, a type of device notorious for its weak security. In short, the team created a solution that improves Bluetooth security without sacrificing its performance.